Introduction
File permissions are a fundamental Linux concept that determines who can read, modify or run files and folders. Misconfigured permissions can result in accidental data loss, compromised system security, or service interruption. In this guide, we will describe classic Unix-style permissions and discuss how to manage and interpret them. We will also cover Access Control Lists (ACLs), which provide more granular control.
Linux Permission Basics
Users, Groups, and Others
-
Every file and directory in Linux has an owner and a group. Ownership is displayed using the
ls -lcommand.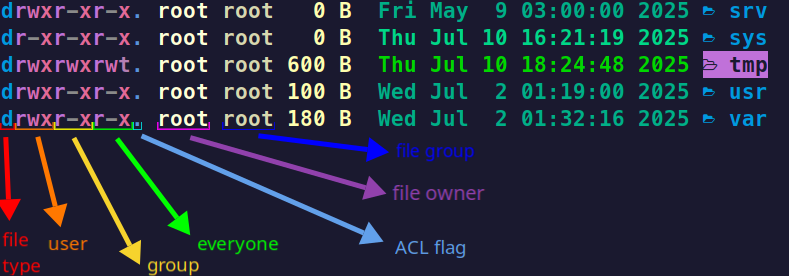
- The first column (red column) shows the file type. Most common types are:
-for regular filesbfor block devicescfor character devicesdfor directorieslfor symbolic linkssfor unix socket files
- The second, third, and fourth columns show the permissions:
rfor read,wfor write,xfor execute (explained in detail below).- If a permission is not granted, it appears as
-. - Orange column shows the user, yellow column shows the group, and green column shows the everyone permissions.
- The fifth column (blue column) shows the additional ACL permissions.
- The sixth column (purple column) shows the file owner.
- The seventh column (brown column) shows the file group.
- The first column (red column) shows the file type. Most common types are:
Permission Bits: r, w, x
- Permissions are represented by three characters:
r,w, andx.- r (read): Allows reading the contents of a file or listing a directory.
- w (write): Allows modifying a file or making changes within a directory (e.g., add/delete files).
- x (execute): Allows running a file as a program or entering a directory.
For example, if a file has permissions rwxr-xr--:
rwxfor the owner (read, write, execute)r-xfor group (read, execute)r--for others (read only)
Numeric (Octal) Representation
- Permissions can also be represented numerically using octal notation, where each
permission bit is assigned a value:
r= 4w= 2x= 1
For example, rwxr-xr-- translates to:
rwxfor the owner (read, write, execute) = 4 + 2 + 1 = 7r-xfor group (read, execute) = 4 + 0 + 1 = 5r--for others (read only) = 4 + 0 + 0 = 4
So, rwxr-xr-- is represented as 754 in octal.
chmod 754 script.shSymbolic Representation (chmod)
- Permissions can also be modified symbolically, using letters to represent the user
categories:
u: user (owner)g: groupo: othersa: all (user, group, others)
For example, to add read and execute permissions for the user, add write permission for the group, and remove execute permission for others, you can use:
u+rx:umeans user (owner)+means add permissionrxmeans read and execute
g+w: Add write for the group.gmeans group+means add permissionwmeans write
o-x: Remove execute for others.omeans others-means remove permissionxmeans execute
You can combine these in a single command:
chmod u+rx,g+w,o-x file.txtSpecial Permission Bits
Other than the standard permissions, Linux has special permission bits that modify behavior. For example:
- Setuid (s): When set on an executable file, it allows the file to run with the permissions of the file owner, rather than the user running it. This is useful for programs that need elevated privileges temporarily. Example:
- Setgid (s): When set on a directory, new files created within that directory inherit the group of the directory, rather than the primary group of the user creating the file. This is useful for shared directories where you want all files to belong to a specific group.
- Sticky Bit (t): When set on a directory, it restricts file deletion within that directory to the file’s owner, the directory’s owner, or the root user.
Access Control Lists (ACLs)
Access Control Lists (ACLs) provide a more flexible permission model than traditional Unix permissions. They allow you to specify permissions for multiple users and groups beyond just the owner and group. Supported by common filesystems like btrfs, ext4, xfs, zfs, and more, ACLs are useful for complex permission scenarios.
Most Common ACL Commands
- getfacl: Get ACLs for a file or directory.
- setfacl: Set ACLs on a file or directory.
Setting and Using ACLs
-
Some files and directories in Linux have ACLs enabled by default. To check if a file has ACLs enabled, you can use the
getfaclcommand: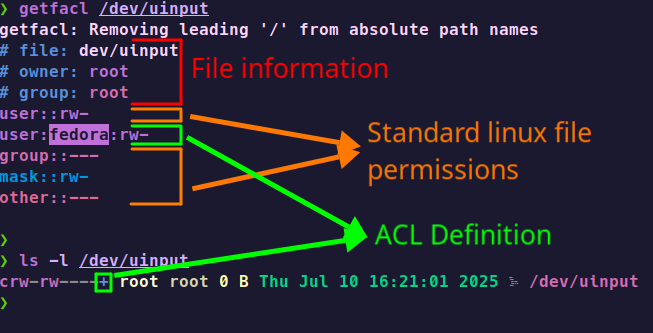
Changing ACLs
-
To set an ACL for a specific user, you can use the
setfaclcommand. For example, to give usertaharead and write permissions on a file nameddata.txt, you can use:setfacl -m u:taha:rw data.txt-mflag stands for modify, indicating that you are modifying the ACL.ustands for user, and in this case, it specifies that the ACL is being set for the usertaha.rwspecifies the permissions being granted, which are read and write.
-
Another example is to set an ACL for a specific group. For example, to give the group
developersread and execute permissions on a directory namedproject, you can use:setfacl -m g:developers:rx projectgstands for group, and in this case, it specifies that the ACL is being set for the groupdevelopers.rxspecifies the permissions being granted, which are read and execute.
Differences Between ACLs and Traditional Permissions
| Feature | Traditional Permissions (User/Group/Other) | Access Control Lists (ACLs) |
|---|---|---|
| User/Group Granularity | One owner, one group, others | Multiple specific users and groups |
| Flexibility | Limited to owner, group, others | Fine-tuned, per-user and per-group |
| Permission Assignment | Cannot assign different permissions to multiple users/groups | Can assign different permissions to multiple users/groups |
| Use Case | Simple access control | Complex, collaborative environments |
Conclusion
Understanding Linux permissions is essential for maintaining system security and managing access to files and directories. By mastering both traditional permission schemes and Access Control Lists (ACLs), you can tailor access controls to fit a wide range of scenarios, from simple personal projects to complex, collaborative environments. Regularly reviewing and adjusting permissions helps prevent unauthorized access and protects your data. With these tools and concepts, you are well-equipped to manage permissions effectively on any Linux system.